Summer School 2024: Usable Security
Summer School 2024: Usable Security
APPLICATIONS ARE NOW CLOSED!
We are inviting applications from undergraduate, graduate students and researchers in the area of Cybersecurity and related fields. This year's first summer school will be focusing on Usable Security. During our annual scientific event, students will have the opportunity to follow one week of scientific talks and workshops, present their own work during poster sessions and discuss relevant topics in Usable Security with fellow researchers and expert speakers. The program will be complemented by social activities.
Application Process: Please fill in the application form (closed now) and upload your CV, a Motivation Letter, University Certificate of Transcript of Records.
Notification of Acceptance: Several rounds of acceptance, roughly 3 weeks after application at the latest.
Fee: 200,-€ (includes full program, food and beverages during the week, and social activities)
Deadline for Regular Application: June 30, 2024.
Deadline for Late Application: We are accepting applications for our wait list until July 8 2024.
Travel Grant: We are offering travel grants for students who participate actively in the whole event and present their work during a poster session. With your application, you can apply for a grant of up to 500,-€ per person (actual travel cost spent, economy flight, train ticket 2nd class). Please do not book any travel arrangements before you have been selected by our jury and accepted to our Summer School. After acceptance, please send your travel arrangements to cysec-lab@cispa.de for approval prior to booking anything. We will confirm if/that your expenses will be covered and you will be reimbursed after completing the Summer School successfully.
Presentations: There will be at least one session, during which participants can present their own work / scientific poster. The presentation is not mandatory to receive a certificate of attendance, but we are highly encouraging you to contribute your work to this session and as it will provide you with valuable feedback from an expert audience and might kindle interesting discussions.
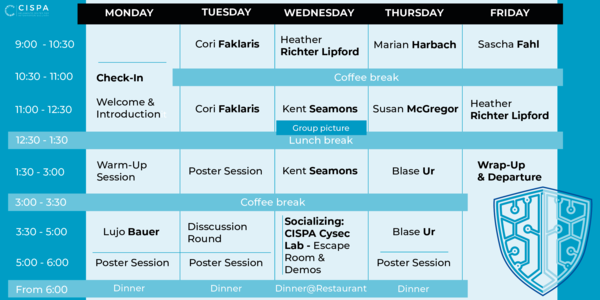
When: July 22 - 26, 2024
Where: CISPA - Helmholtz Center for Information Security, Saarbruecken.
Blase Ur (University of Chicago)
Title 1: How Can Privacy Exist in a Data-Driven World?
Abstract: Huge amounts of personal data underpin the algorithms that drive modern life. How can privacy exist in such a world, and what does privacy even mean in this context? In this talk, I will partially answer these questions by discussing how our group employs data-driven methods to help users understand how their data is collected and used. In particular, I will present tools we have developed both to provide transparency about online tracking and to help users engage with the personal data companies hold about them. To further contextualize the meaning of privacy, I will describe user studies investigating how privacy is perceived. I will conclude by describing our ongoing collaborations with artists to recenter privacy as a societal value.
Title 2: Passwords: Modeling Them, Reusing Them, and Eliminating Them
Abstract: For over a decade, I have studied various aspects of authentication ecosystems. I will first briefly discuss my initial journey modeling passwords and helping users create better passwords. The focus of the talk will be a measurement study we performed of the University of Chicago's vulnerability to credential-guessing attacks across twenty years. We collaborated with our university's IT Security team to retrospectively analyze the degree to which both reused passwords (when a user employs similar credentials across different sites) and common passwords put our users at risk. Given a list of university usernames, we searched for matches in data breaches from hundreds of websites. After cracking hashed passwords and tweaking guesses, we successfully guessed passwords for 32.0% of accounts matched to a university email address in a data breach, as well as 6.5% of accounts where the username (but not necessarily the domain) matched. I will conclude my talk by discussing our current investigations of FIDO2 passwordless authentication, including a forthcoming paper qualitatively studying why passkeys have not yet "killed" the password for web authentication.
Short Bio: Blase Ur is an Associate Professor of Computer Science at the University of Chicago, where he researches computer security, privacy, human-computer interaction, and ethical AI. His lab, the UChicago SUPERgroup, uses data-driven methods to make complex computer systems more usable and to help users make better security and privacy decisions. He has received an NSF CAREER Award, Quantrell Award for Undergraduate Teaching, five best/distinguished paper awards, and five honorable mention paper awards. He has also received the Allen Newell Award for Research Excellence, SIGCHI Outstanding Dissertation Award, IEEE Cybersecurity Award for Practice, and a Fulbright scholarship to Hungary. He holds degrees from Carnegie Mellon University (PhD and MS) and Harvard University (AB). He also likes bicycles, cacti/succulents, and punk rock.
Heather Richter Lipford (University of North Carolina at Charlotte)
Title: Usable Security and Privacy in the Age of Smart Spaces
Susan E. McGregor (Columbia University)
Title: Culture and Cognition: Developmental and Sociocultural Components of Usable Security for Kids
Abstract: Networked technologies are a common - and increasingly mandatory - part of children's home and school environments, shaping their security and privacy perceptions from a young age. Designing usable security systems for children, schools and families, however, requires engaging with the unique sensorimotor, cognitive and other developmental capacities of younger users. Likewise, because concepts and values around privacy and security vary across cultures and contexts, supporting meaningful choices about how to manage security and privacy for children while scaffolding their broader awareness of these issues is essential. In this talk, I will reflect on recent work in this area, as well as future research directions and ideas for working with schools, families and children.
Cori Faklaris (University of North Carolina at Charlotte)
Title: Connecting Attitudes and Social Influences with Designs for Usable Security and Privacy
Abstract: Many system designs for cybersecurity and privacy have failed to account for individual and social circumstances, leading people to use workarounds such as password reuse or account sharing that can lead to vulnerabilities. To address the problem, researchers are building new understandings of how individuals’ attitudes and behaviors are influenced by the people around them and by their relationship needs, so that designers can take these into account. In this talk, I will first share my research to connect people’s security attitudes and social influences with their security and privacy behaviors. As part of this, I will present the Security and Privacy Acceptance Framework (SPAF), which identifies Awareness, Motivation, and Ability as necessary for strengthening people’s acceptance of security and privacy practices. I then will present results from my project to trace where social influences can help overcome obstacles to adoption such as negative attitudes or inability to troubleshoot a password manager. I will conclude by discussing my current work to apply these insights to mitigating phishing in SMS text messages (“smishing”).
Lujo Bauer (Carnegie Mellon University)
Title: Toward more secure and more usable text passwords: Data and metrics and AI, oh my!
Abstract: Text passwords have long been the dominant form of authentication in computer systems. Unfortunately, they can be hard to remember, inconvenient to type in, and, worse yet, we're supposed to have a unique password for each of hundreds of accounts! This talk will describe a decade-long quest to scientifically determine how to make text passwords both more usable _and_ more secure. The talk will discuss both innovations in _how to conduct_ passwords research, including how to measure password strength and how to test passwords ideas in an ecologically valid way, and the results -- now incorporated in widely used authentication standards -- of applying these methods to study the passwords created by tens of thousands of study participants. The talk will also give participants an inside view of how the research developed, such as where the original research idea came from, how research questions changed from one paper to another, the ethics of using stolen passwords, and more.
Title 2: Kick-off talk on "Home IoT & Stalking" in Tuesday's discussion round
Short bio: Lujo Bauer is a Professor of Electrical and Computer Engineering, and of Computer Science, at Carnegie Mellon University. His research spans many topics in computer security and privacy, from web tracking and information-flow control to formal methods and the privacy risks of new technologies. His current research projects include finding and fixing flaws in practical uses of ML like face recognition and autonomous driving; building tools to help make smart homes
better protect the security of both residents and bystanders; and measuring the harms caused by online tracking.
Lujo served or serves as program (co-)chair of top security conferences like IEEE S&P (2015), NDSS (2014), USENIX Security (2025); as well as of SOUPS (2013, 2014), the top venue focusing on usable security and privacy.
Kent Seamons (Brigham Young University)
Title 1: Usability Challenges and Emerging Research in Secure Messaging
Abstract: Billions of people rely on secure messaging apps with centralized key management, making them vulnerable to fake key attacks. Although an authentication ceremony exists to detect such attacks, it is rarely used. This talk will review research focused on improving the usability of the authentication ceremony. Additionally, we explored innovative approaches to automatically detect these attacks without user involvement, which introduces new usability challenges. Finally, we will delve into recent research examining user perceptions and expectations regarding message deniability, an often overlooked aspect of secure messaging.
Title 2: Usability Pitfalls in Two-Factor Authentication
Abstract: Passwords are notoriously inadequate for securing account access. Two-factor authentication (2FA) enhances security by requiring both a password—the primary authentication factor—and an additional device or resource that is difficult to steal. This talk will examine our efforts to understand and improve 2FA usability, addressing challenges with account setup that hinder implementation, initiatives to streamline bulk enrollment and deletion of authenticators, and our investigation into local attacks on 2FA where insufficient alerts fail to warn users of successful breaches. We will discuss the implications of these findings for emerging passwordless authentication methods.
Short Bio: Kent Seamons is a Professor of Computer Science at Brigham Young University. His research focuses on usable security, privacy, authentication, and end-to-end encryption. Under his mentorship, students have received prestigious awards, including the John Karat Usable Privacy and Security Student Research Award, the Internet Defense Prize First Runner-Up, a CHI Honorable Mention, and a SevDev Best Paper award. Kent earned his PhD from the University of Illinois, where he was honored with the David J. Kuck Outstanding Doctoral Thesis Award. He enjoys hiking, playing the piano and organ, pickleball, and spending time with his wife and their seven grandchildren.
Marian Harbach (Google)
Title: Trust & Safety UX Research in Chrome
Abstract: In this talk, Marian will introduce how User Experience Researchers work at Google in general and within Chrome Trust & Safety in particular, before presenting several case studies of recent work he completed in the web permissions space. These include how we think about permissions UX in general, what the current user behavior and sentiment on permission prompts in desktop browsers is, and how we deal with websites having suboptimal permissions experiences in the absence of an app store enforcing policies. Finally, he will provide an overview of how we plan to further improve the permissions experience on the web.
Title: Human Factors in Secure Software Development
Abstract: This talk will illustrate the needs and benefits of human factors research in secure software development. Securing open and closed software systems requires recognizing the criticality of individual developers and organizations. While providing secure technologies and tooling is essential, developers are a commonly promising attack vector, and their behavior and practices significantly impact overall software security. Sascha will illustrate recent research findings in this area and discuss challenges and opportunities for future research.
Title: Kick-off talk on "Passwordless Authentication" in Tuesday's discussion round
Please have a look at last year's school, Summer School 2022, or our Digital Summer School 2021 to get a general idea of the event.
If you have any questions or queries, our Summer-School team will be glad to help via summer-school@cispa.de.
If you want to be informed about scientific events and regular summer schools, please register to our newsletter:
Yes, if you attended one of our Summer Schools, of course you are welcome to apply for any of the following years. If there are two Summer Schools in one year, you can apply for both Summer Schools. It is advisable to mention a specific research focus in your application that aligns with your interests and your prior education.
Our jury selects the participants of the Summer Schools. We have strict criteria for selecting participants for our Summer School due to the high number of applications compared to the limited available spots. We give priority to those currently studying or with a background in the Summer School's topic. A foundational knowledge in the field is required, and participants should have reached a certain academic level. For instance, individuals in the early stages of a Bachelor's degree may not qualify. This is important because the Summer School is interactive, and having prior knowledge is crucial for active participation.
You can apply for a travel grant during your application if your travel costs are not reimbursed by your employer. Our jury will select participants and approve the travel grant within availability. You will only receive reimbursement after successful completion of the Summer School which means actively attending every day of the event. Another requirement for reimbursement is that you actively participate in the Summer School by presenting a poster during the poster session. There might be additional requirements for a specific Summer School which will be mentioned on the event’s website. If your travel grant was approved you need to hand in receipts after completion of the Summer School for all expenses in connection with your travels. The grant is limited to 500€ unless stated otherwise on the event’s website. The participation fee secures your spot for the event and covers catering, drinks, course materials and the full program. Thus it cannot be refunded via the travel grant. Only receipts dated within one day before the start of the event until the last day are eligible for reimbursement. Exceptions require prior approval via email. Please book accommodations from our recommendation list when possible or contact us for approval prior your booking.
Your poster should be in portrait format, A0 size, please bring your printed poster with you. If you don’t have the possibility to print it yourself, send it as a PDFX file via email to us within the deadline mentioned being accepted to our event. Each presentation will be limited to 5 minutes, followed by a short discussion.
If you have specific dietary restrictions, please include that information in your application. We strive to accommodate all dietary needs to the best of our ability. Additionally, rest assured that there is always a vegetarian option available for individuals with restrictions concerning meat.
Bring your own laptop. Course materials and catering during the event will be provided and is included in the fee. You will receive handouts and presentations after the event of every speaker who agreed to distribute them.
Yes, a certificate will be provided if you successfully attend all days of the Summer School.
We can only reimburse costs for participants. If you bring your partner or a friend to share your hotel room, please provide receipts and comparison prices for the expenses that would have occurred if you traveled alone, and we will reimburse accordingly.
Both individuals should ensure the hotel receipt includes both names. Submit this receipt, and each of you will receive half the reimbursement for the hotel room cost.
If you cancel at short notice after confirming and paying the participation fee, refunds cannot be issued. You can, however, name a substitute participant with similar qualifications. Refunds are contingent on having enough time to rearrange event planning (e.g. transport and catering).