TYPE
Live Demo
TOPIC
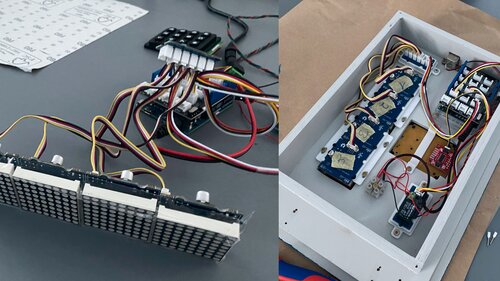
Side-channel attacks
YEAR
2023
SOFTWARE
Figma, Adobe Photoshop, Adobe Illustration, Adobe InDesign, Affinity Designer, Autodesk Fusion360, PlatformIO, VS Code, Scrivener
HARDWARE
Wooden Enclosure: Team SciEng Custom-Built, Miter Saw, Disc Sander, Painting
ELECTRONICS
Arduino Leonardo, Sparkfun / Seeed Studio I²C Components, 3D-printed mounts (Thingiverse, Team SciEng Custom Design), passive components
SKILLS
Visual Design, Communication Design, Rapid Prototyping, CAD, Hardware Architecture, Software Engineering, Woodworking, 3D Printing, Storytelling